One of the critical considerations when outsourcing/offshoring any aspect of your business is the cyber-security of your service vendor (“Vendor”) – because it’s probably your weakest link. In this article we summarize the risks and set out steps for reviewing mitigation of those concerns.
Ten years ago, mostly of this risk revolved around the physical security necessary to prevent staff from being bribed or otherwise coerced to steal private data. A tour around any outsource center today will confirm extraordinary attention to physical security, including the common requirement for staff to leave their smartphones in a ‘cage’ at the door before entering for work, and a requirement for each employee to swipe individually through a control door (i.e. strictly no tail-gating).
Roll-forward to 2019 and the danger of data loss is substantially magnified while in some jurisdictions the requirement to ‘fess up’ to Cyber breaches may be looser than in your home market.
AT Kearney in their 2019 report states:
“The increasing incidence of cyber attacks and their catastrophic impact has taken cyber security right to the board agenda. A.T. Kearney’s analysis indicates that the incidence of cyber attacks on organizations has been accelerating at approximately 40 percent over the past three years.”
If the Vendor you have appointed is in a less-developed market, where typically the labor-arbitrage benefit is the highest, the probability of an enterprise-level cyber-attack is the highest it ever been.
In its Global 2019 Security Bulletin, Kaspersky Security Network (KSN) showed that the risk by location is increased where:
- Markets have a high usage of social media, leading to ‘social engineering’ attacks
- Markets that continue to use ‘unprotected’ removable media such as USB or DVD
- Markets where widespread copying of licensed software/media is endemic
As reported by KSN, the top five markets by number of cyber-attacks against users of their security products in 2018 included the Philippines – a leading provider of outsourced services. While attacks on regular computer users don’t necessarily translate directly to at the enterprise level, the statistics are certainly an amber alert for that possibility.
KSN also revealed in their report that its users in the Philippines were attacked by cyber criminals through a popular attack which attempts to infect users’ computers and devices when a surfer visits a website that they didn’t know was infected, thereby installing a malicious script by stealth. Another technique that cyber criminals use is social engineering; research company Statista reports that the penetration rate of social media worldwide exceeds 70% in some parts of Asia and Eastern Europe. In this attack method, criminals convince an unsuspecting user into sending to them their confidential data, facilitating theft or malware installation by opening links to infected websites.
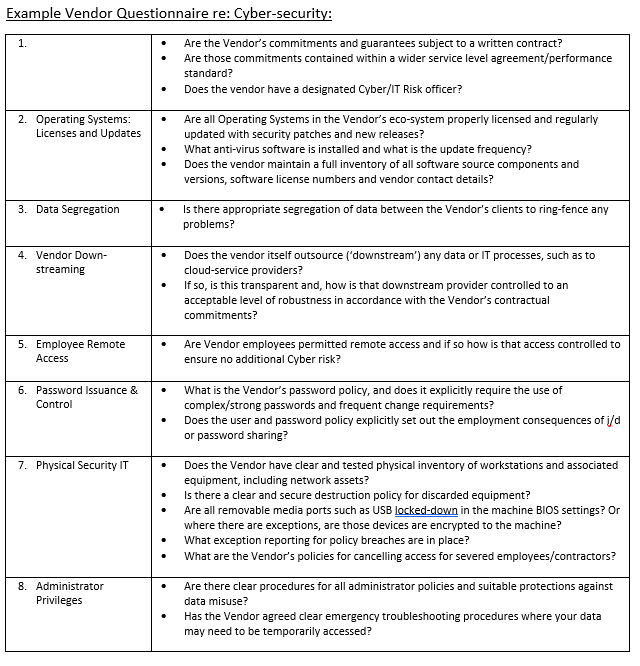
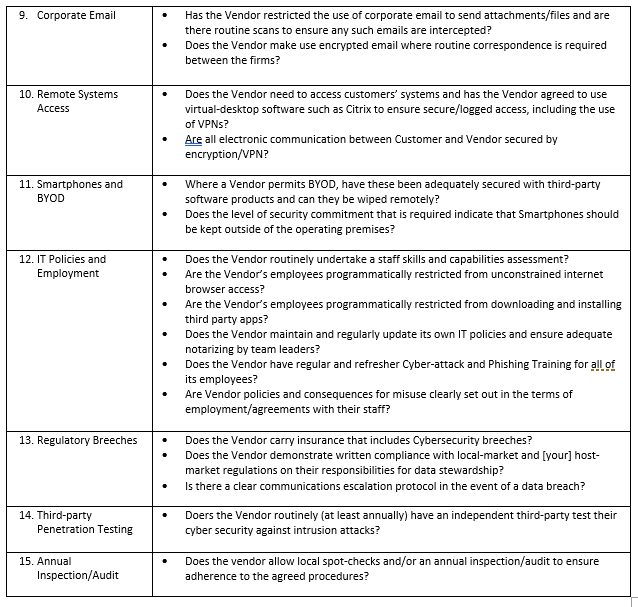
It is therefor of vital importance that when considering an outsource vendor, or renewing a long-standing arrangement, that your due diligence includes a very specific review of the Vendor’s cyber-security defense practices. The American Institute of CPAs publishes a very useful checklist, which we have modified and expanded (as below) from our own experiences. There are many aspects to ensuring your Vendor has a secure operating environment and here are a few of the key questions you can ask: